In the time it takes you to read this sentence, millions of digital interactions have already occurred across the globe. The modern digital landscape is a buzzing hive of constant activity, with staggering volumes of data being generated, shared, and consumed every minute of every day.
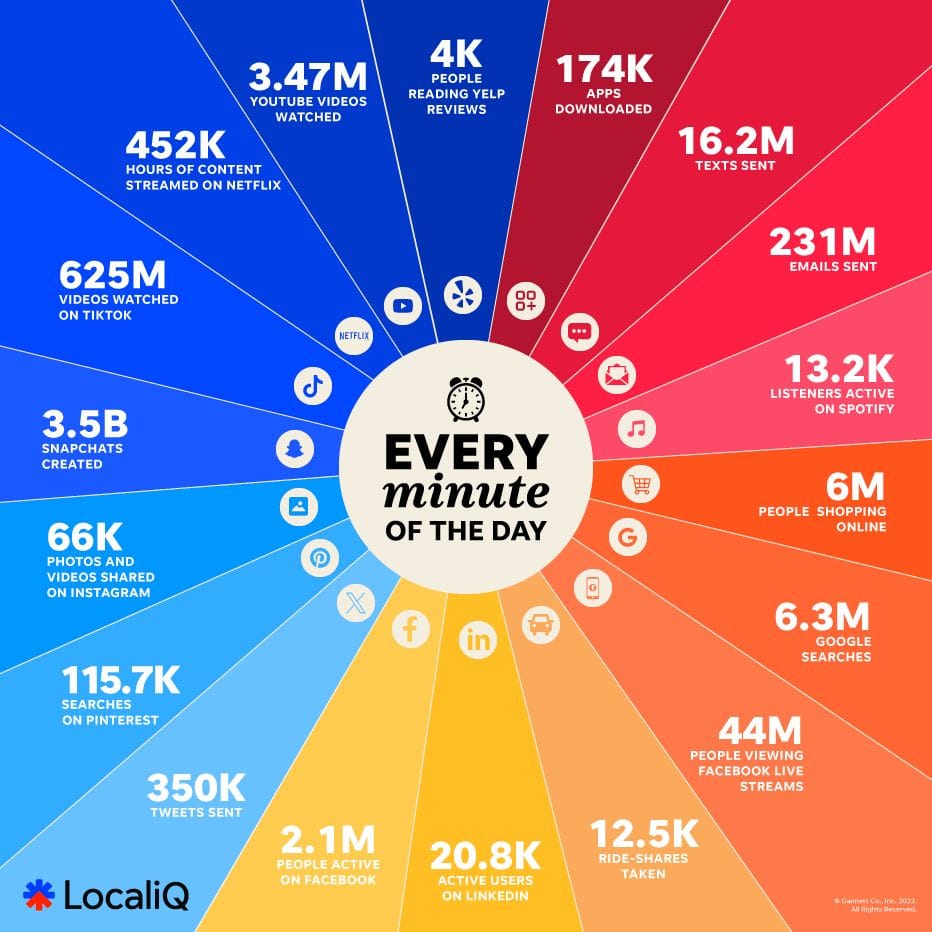
The Digital Minute: By the Numbers
A recent visualization by LocaliQ reveals the true scale of our digital footprint. Every minute:
- 3.5 billion Snapchats are created- 625 million videos are watched on TikTok- 452,000 hours of content are streamed on Netflix- 3.47 million YouTube videos are watched- 4,000 people are reading Yelp reviews- 174,000 apps are downloaded- 16.2 million texts are sent- 231 million emails are sent- 13,200 listeners are active on Spotify- 6 million people are shopping online- 6.3 million Google searches are performed- 44 million people are viewing Facebook Live streams- 12,500 ride-shares are taken- 20,800 active users are on LinkedIn- 2.1 million people are active on Facebook- 350,000 tweets are sent- 115,700 searches occur on Pinterest- 66,000 photos and videos are shared on Instagram
These numbers represent just a snapshot of our digital activities, but they highlight an important reality: with every interaction, we’re generating data that tells a story about our preferences, behaviors, and habits.
What Happens to Your Data?
Behind each statistic lies a more complex story about data collection, processing, and monetization. When you stream content, search for information, or interact on social media, you’re not just consuming a service—you’re participating in a data exchange.
Companies collect this information to:
- Personalize your experiences- Target advertising more effectively- Improve their products and services- Make business decisions based on user behavior- In some cases, sell or share with third parties
The Privacy Dilemma: Data Brokers, Cambridge Analytica, and Photo Metadata Exploitation
The Privacy Paradox
Despite growing awareness about data privacy, most of us continue our digital behaviors without much change—a phenomenon known as the “privacy paradox.” We express concerns about our data while simultaneously engaging in activities that expose it.
Consider that while you may worry about privacy, you’re likely among the:
- 6 million people shopping online each minute, sharing payment information and purchase history- 16.2 million sending text messages, often containing personal information- 231 million sending emails that may include sensitive data- 3.5 billion Snapchat creators, often sharing location data and personal moments
Taking Control of Your Digital Footprint
Understanding the scale of data generation is the first step toward more mindful digital citizenship. Here are actionable steps to better manage your data privacy:
1. Audit Your Digital Presence
Review which platforms have your data and what permissions you’ve granted them. Consider the 44 million people viewing Facebook Live or the 2.1 million active on Facebook—are you sharing more than necessary?
2. Understand Privacy Policies
Before joining the 174,000 app downloads per minute, read the privacy policies to understand how your data will be used.
3. Use Privacy Tools
Employ privacy-focused browsers, VPNs, and search engines that don’t track your activity unlike the services handling 6.3 million Google searches every minute.
4. Be Selective About Sharing
Think twice before becoming one of the 66,000 Instagram shares or 350,000 tweets per minute. Once information is online, it’s difficult to truly delete.
5. Regular Privacy Check-ups
Platforms frequently update their privacy settings. Schedule regular reviews of your privacy configurations.
The Value Exchange
It’s important to recognize that many of the services we use are “free” because our data has value. The 625 million TikTok videos watched every minute are supported by an advertising model built on user data. The question becomes: is the value you receive worth the data you provide?
Data Breaches and Identity Theft: What to Do When Your Personal Information is Compromised
The NSA and the Power of Metadata
While we often focus on the content of our digital communications, government surveillance programs have demonstrated the immense value of metadata—data about data. The National Security Agency’s programs revealed by Edward Snowden in 2013 showed how metadata collection can be used to build detailed profiles of individuals without ever accessing the content of their communications.
Consider that every minute:
- 231 million emails are sent, each with metadata about sender, recipient, time, and location- 16.2 million texts create similar digital trails- 6.3 million Google searches reveal intent and interests- 12,500 ride-shares document precise movements
This metadata, when aggregated, can reveal extraordinarily detailed patterns about an individual’s life—their social networks, daily routines, locations, interests, and behaviors. Unlike content, which may require warrants to access in many jurisdictions, metadata has historically received fewer legal protections despite its revealing nature.
The scale of potential surveillance becomes apparent when we consider the volume of data generated every minute. Programs like PRISM and XKeyscore were designed to filter, analyze, and store vast quantities of this information, enabling retroactive analysis of patterns and connections between individuals.
For the average user, this raises important questions: How much of your digital footprint is being collected? Who has access to your patterns of behavior? And importantly, what protections exist for this revealing metadata?
Social Media Stalking: How Much Does Facebook Really Know About You?
Cambridge Analytica: When Data Becomes Vulnerability
The Cambridge Analytica scandal of 2018 represents one of the most significant examples of how seemingly innocuous data can be weaponized against users. Through a personality quiz app, the company gained access to the data of approximately 87 million Facebook users—many who never directly interacted with the app.
This data harvesting operation reveals several critical vulnerabilities in how we interact online:
- The Network Effect: When 2.1 million people are active on Facebook every minute, your data vulnerability isn’t just determined by your choices, but by those in your network.2. Data Aggregation Risks: Cambridge Analytica combined Facebook profile data with other datasets to create detailed psychographic profiles—demonstrating how separate data points can be combined to reveal more than users intended to share.3. Psychological Targeting: The company used this data to target voters with highly personalized political messaging designed to leverage psychological predispositions—showing how data can be used not just to understand but to influence behavior.4. Platform Architecture: The very design of social platforms, which encourage broad sharing and connections, can create structural vulnerabilities that users have little control over.
Each time you become one of the 66,000 Instagram shares or 625 million TikTok video views, your data doesn’t just reveal what you like—it potentially provides insight into how you can be influenced. This reality transforms social media engagement from a passive activity into a potential vulnerability point requiring active management.
The Privacy Implications of IoT Security Vendors Sharing Information with Law Enforcement
Data Brokers: The Hidden Market for Your Information
While we’re acutely aware of data collection by the platforms we directly interact with, a less visible but equally significant industry operates in the shadows: data brokers. These companies collect, aggregate, and sell personal information about consumers, often without direct interaction with the individuals whose data they trade.
The scale of this industry becomes apparent when we consider the statistics from our digital minute:
- Data from 6.3 million Google searches can be aggregated to reveal consumer intent- 6 million online shopping transactions create valuable purchase behavior profiles- 66,000 Instagram shares and 3.47 million YouTube views generate engagement data that reveals preferences- 12,500 ride-shares create precise location histories
Data brokers collect this information from various sources, combine it with offline data, and create detailed profiles that can include:
- Demographic information- Financial data- Health interests- Political affiliations- Purchase history- Property records- Online and offline behavior patterns
These profiles are then packaged and sold to marketers, insurers, financial institutions, and other businesses looking to make data-driven decisions. The data broker industry operates with minimal transparency, with the average consumer unaware of how many companies hold their information or how to access and control it.
The Complete Guide to Social Media Privacy: Protecting Your Digital Life in 2025
Beyond 2025: The Evolving Landscape of Online Privacy
As we look toward the latter half of the 2020s, several emerging trends and technologies will reshape how we understand and manage online privacy:
- Decentralized Identity Systems: Blockchain and other decentralized technologies may enable users to own and control their identity data, potentially shifting power away from centralized data collectors.2. AI Privacy Guardians: Advanced AI systems could emerge as privacy advocates, automatically negotiating data sharing terms, detecting privacy vulnerabilities, and managing consent on behalf of users.3. Regulatory Convergence: We may see international privacy frameworks begin to align, creating more consistent protections regardless of geographic location.4. Privacy-Enhancing Technologies (PETs): Techniques like federated learning, differential privacy, and homomorphic encryption could allow companies to derive insights from data without accessing personal information directly.5. Data Dignity Movement: Beyond mere privacy, a broader movement advocating for fair compensation for data may gain traction, treating personal information as a resource that deserves payment when used.6. Ambient Privacy Challenges: As IoT devices, smart cities, and augmented reality technologies proliferate, new questions will arise about privacy in shared physical spaces where opting out becomes increasingly difficult.7. Post-Cookie Attribution: With the decline of third-party cookies, new tracking and attribution methods will emerge, potentially bringing both privacy benefits and new unexpected vulnerabilities.
The sheer volume of data generated every minute—from 231 million emails to 625 million TikTok videos—means that privacy will likely remain a complex negotiation between individual rights, business interests, and social values. The companies that thrive in this environment will be those that recognize privacy not as a compliance burden but as a fundamental user expectation.
Ensuring Child Safety on TikTok: A Closer Look at Differentiated Experiences
Looking Forward: The Future of Data Privacy
As regulations like GDPR and CCPA evolve, and as consumers become more privacy-conscious, we may see shifts in how companies approach data collection. Some positive trends include:
- Increased transparency about data collection practices- More granular control over personal data- Privacy-by-design approaches becoming standard- The rise of privacy as a competitive advantage
🎧 Related Podcast Episode
Conclusion
Every minute of the day, billions of digital interactions create a complex web of data flows. By understanding the scale of this activity and taking proactive steps to manage your privacy, you can enjoy the benefits of our connected world while maintaining greater control over your personal information.
The next time you become one of the millions watching YouTube videos or sending an email, remember that each action contributes to your digital footprint. Making informed choices about your data isn’t about disconnecting—it’s about connecting on your own terms.
